Paul Haskell-Dowland, Edith Cowan University
On Sunday afternoon, Channel 9 posted a cryptic tweet indicating it was under attack. The accompanying video acknowledged that the failure to run the Weekend Today show that morning was attributed to a major cyber incident.
Reporting also confirmed the situation had affected the network’s ability to “produce its news and current affairs content”.
Emails and editing systems were all impacted by the incident, in what was described as an unprecedented attack against a mainstream media organisation in Australia. In a follow-up article, 9 News described the outage as a “sophisticated and calculated attack” that has “fundamentally disrupted how the network delivers and presents news”.
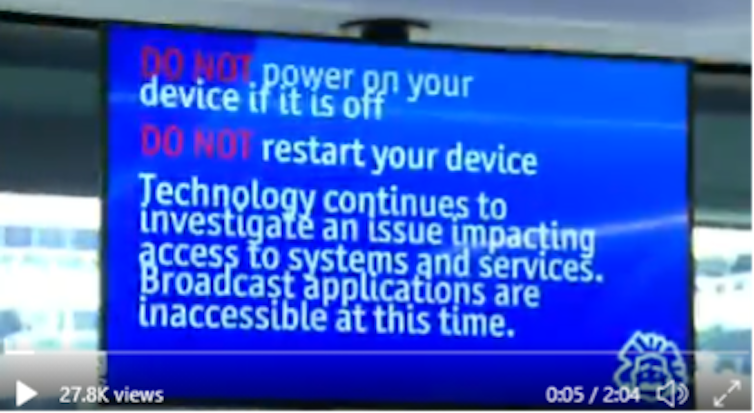
The disruption was so significant that many Channel 9 staff were instructed to work from home. They were also warned to avoid turning on or restarting computers until the problems were addressed.
As is often the case in the early stages of a major cyber incident, details are scarce, and it’s very hard to know who is behind it.
What happened?
There is no official statement of cause, but it is clear that malware spread between devices at Channel 9’s Sydney headquarters, leaving data and production systems inaccessible.
The speed with which the malware spread through system may indicate a concerted effort to misuse Channel 9’s systems. Some experts have pointed to the possibility of fraudulent “IT updates” being sent out to users’ computers to spread the infection. This suggests the attacker(s) may have had prolonged access to Channel 9’s systems before the events on Sunday.
Although live television broadcasts resumed quickly, it is likely that a full recovery behind the scenes will take considerably longer. It could potentially cost significant time and money to fix the existing problems and address the underlying vulnerabilities that allowed the attack to be so effective.
How did it happen?
Ransomware attacks often start with a phishing attack, in which large numbers of emails are sent to staff at an organisation.
These emails often replicate the look of a legitimate message, and can include seemingly privileged information (such as staff names and internal departments) in an attempt to appear genuine.
These emails aim to deceive individuals into clicking on a link or installing a file, perhaps by claiming this is a necessary patch to repair an issue with their computer.
Once installed, ransomware will typically encrypt important files or even entire systems, rendering them inaccessible. The malware will often target common file types such as Word documents, PDFs, spreadsheets or emails.
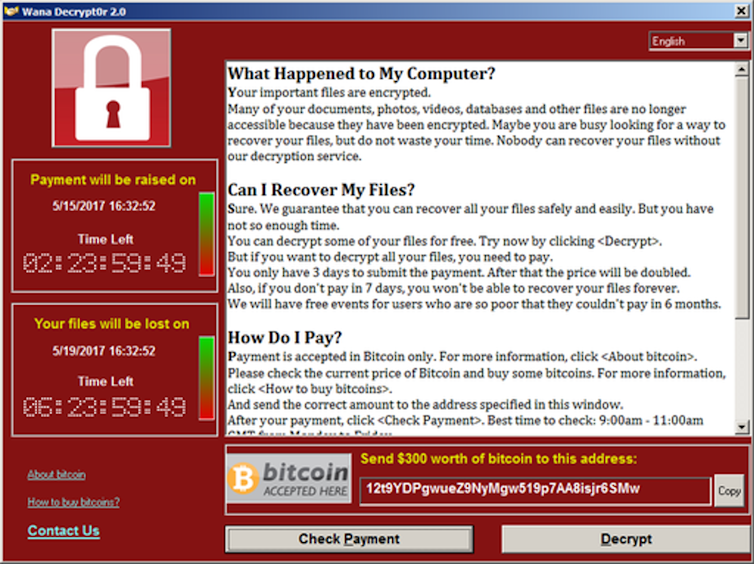
Many cyber-criminals have a financial motive, and will typically ask for a ransom in exchange for releasing the locked-out data. The “key” to unlock the data will usually be transmitted to a remote server and then deleted from the compromised system.
Another possibility is cyber-sabotage by a foreign state actor. In this context, the attack may be meant as a statement, retribution, or have some other political motivation. In such cases, it is probable that the “key” used to encrypt data is discarded on creation, rather than kept as a bargaining chip. This is distinct from financial cyber-extortion, as the intent is to wreak havoc by permanently denying access to the resources (thus this malware is sometimes referred to as “wiperware”).
Who is to blame?
Although it is too early to definitively attribute blame, media reports have pointed to a foreign state actor. This theory is bolstered by Nine’s statement that “ransomware was used but no ransom demanded”.
Previous state-sanctioned attacks have been attributed to a range of countries, including China, Iran and North Korea. But Russia is considered the most likely aggressor in this instance.
It has been alleged that this attack is a retaliation for Channel 9’s screening of an exposé on politically motivated poisonings attributed to the Russian government.
What next?
Addressing these incidents requires a careful approach. Limiting the spread of the malware is crucial — hence the instruction to staff to avoid turning on devices.
It is also important to identify the specific vulnerability that was exploited, to prevent future outbreaks. If data have been deleted (or rendered permanently inaccessible), backups will need to be retrieved.
While the focus at the moment is on restoring access to systems, the company will also need to conduct a forensic examination of the attack, to ensure lessons are learned.
While Australian news outlets have often reported on previous cyber-attacks, this incident is a wake-up call that they are not immune from becoming targets themselves.
Paul Haskell-Dowland, Associate Dean (Computing and Security), Edith Cowan University
This article is republished from The Conversation under a Creative Commons license. Read the original article.